Improving AI-based defenses to disrupt human-operated ransomware
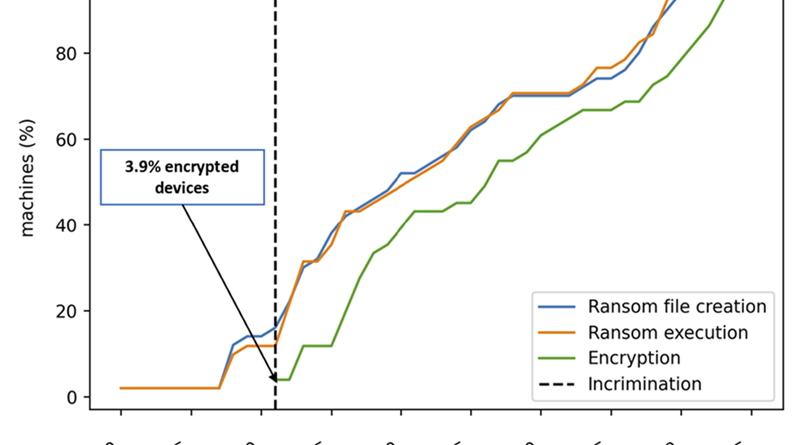
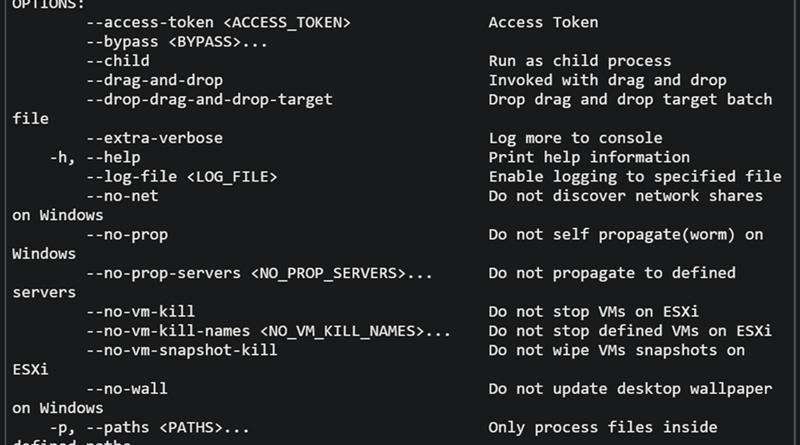
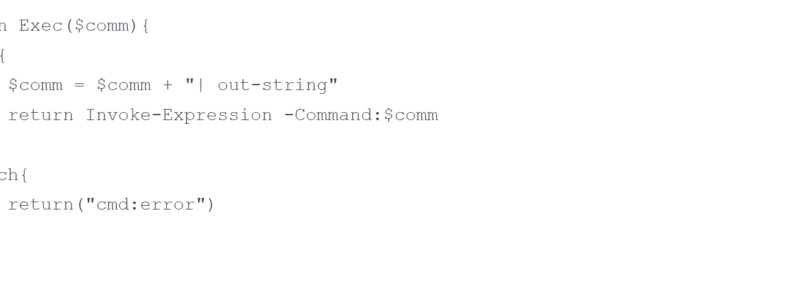
To disrupt human-operated ransomware attacks as early as possible, we enhanced the AI-based protections in Microsoft Defender for Endpoint with a range of specialized machine learning techniques that swiftly identify and block malicious files, processes, or behavior observed during active attacks.
The post Improving AI-based defenses to disrupt human-operated ransomware appeared first on Microsoft Security Blog. READ MORE HERE…