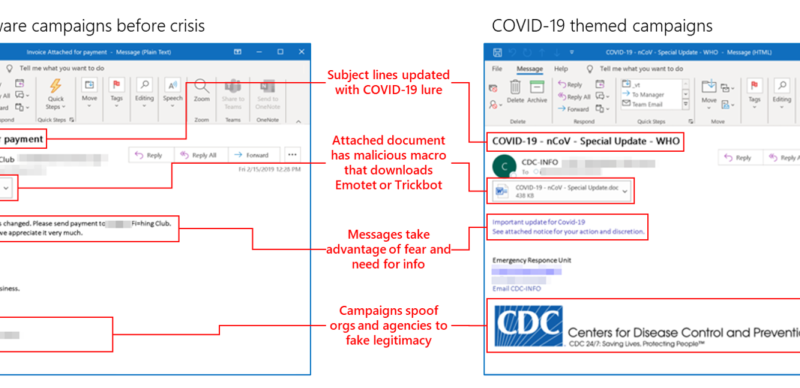
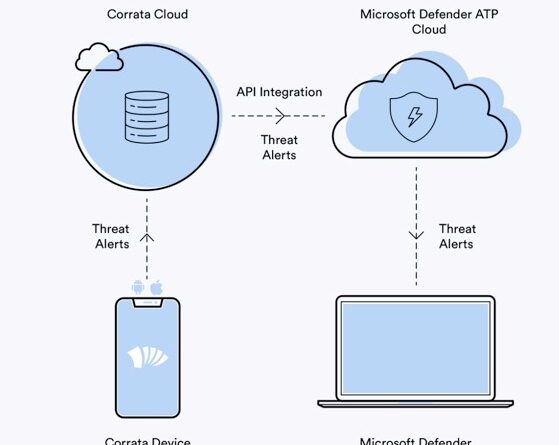
Simply stated, zero trust calls for verifying every user and device that tries to access the network and enforcing strict access-control and identity management that limits authorized users to accessing only those resources they need to do their jobs.Zero trust is an architecture, so there are many potential solutions available, but this is a look at those that fit in the realm of networking.[Get regularly scheduled insights by signing up for Network World newsletters.]
Least privilege
One broad principle of zero trust is least privilege, which is granting individuals access to just enough resources to carry out their jobs and nothing more. One way to accomplish this is network segmentation, which breaks the network into unconnected sections based on authentication, trust, user role, and topology. If implemented effectively, it can isolate a host on a segment and minimize its lateral or east–west communications, thereby limiting the “blast radius” of collateral damage if a host is compromised. Because hosts and applications can reach only the limited resources they are authorized to access, segmentation prevents attackers from gaining a foothold into the rest of the network.To read this article in full, please click here READ MORE HERE…
Read More