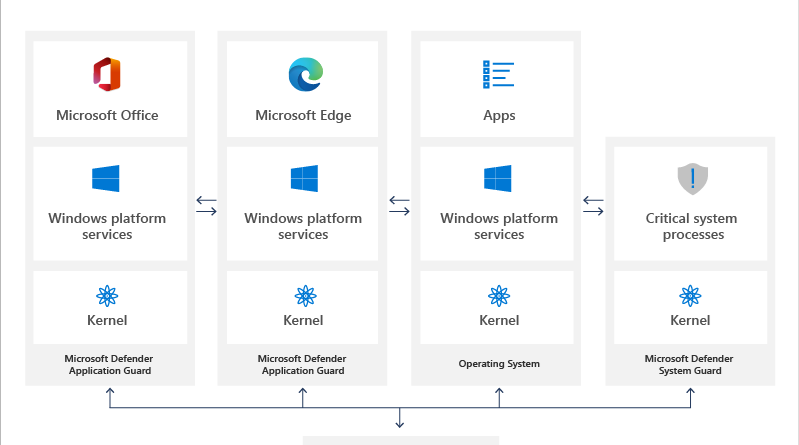
Defend against zero-day exploits with Microsoft Defender Application Guard
Zero-day security vulnerabilities are like gold to attackers. With zero-days, or even zero-hours, developers have no time to patch the code, giving hackers enough access and time to explore and map internal networks, exfiltrate valuable data, and find other attack vectors.
The post Defend against zero-day exploits with Microsoft Defender Application Guard appeared first on Microsoft Security Blog. READ MORE HERE…