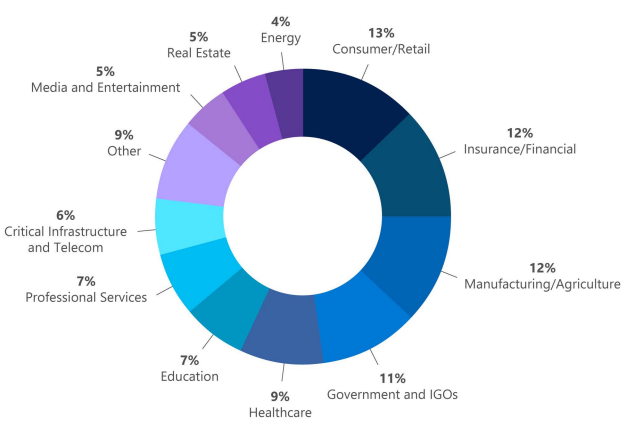
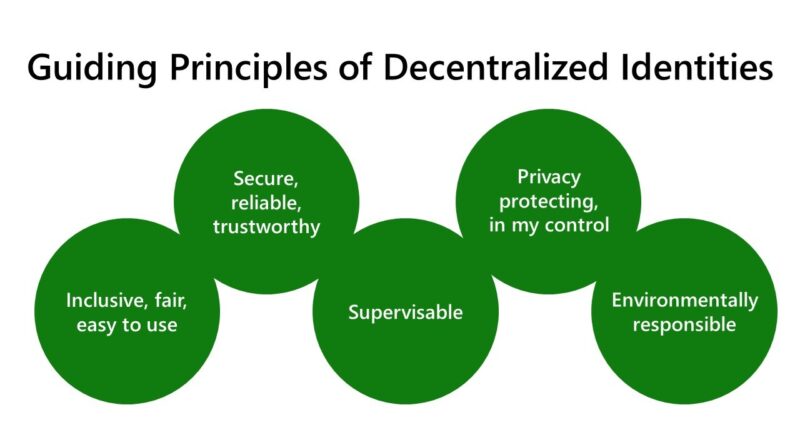
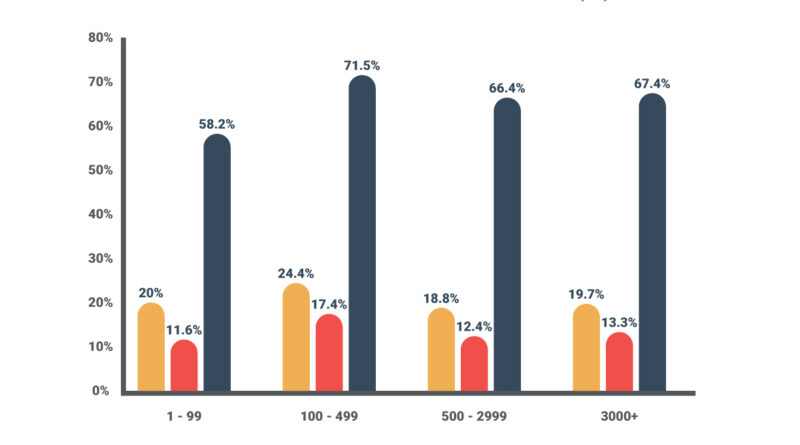
Azure network security helps reduce cost and risk according to Forrester TEI study
As organizations move their computing from on-premises to the cloud, they realize that leveraging cloud-native security tools can provide additional cost savings and business benefits to their security infrastructure. Azure network security offers a suite of cloud-native security tools to protect Azure workloads while automating network management, implementing developer security operations (DevSecOps) practices, and reducing the risk of a material security breach.
The post Azure network security helps reduce cost and risk according to Forrester TEI study appeared first on Microsoft Security Blog. READ MORE HERE…