Microsoft shares 4 challenges of protecting sensitive data and how to overcome them
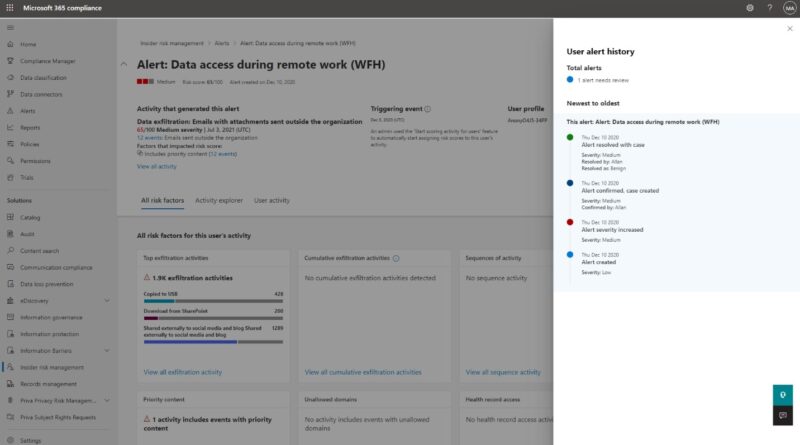
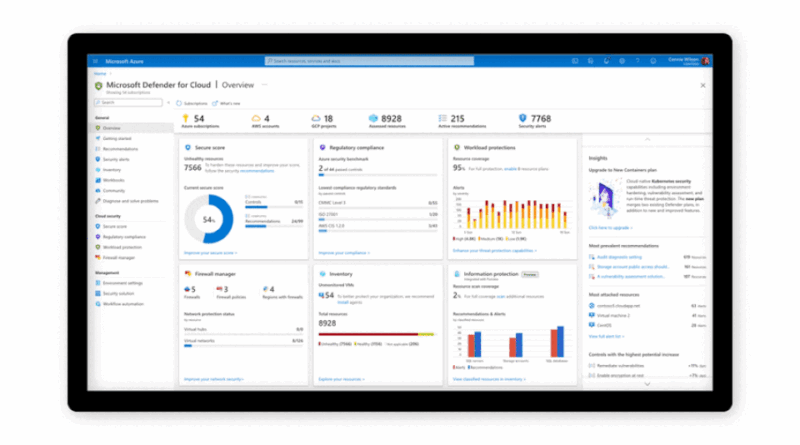
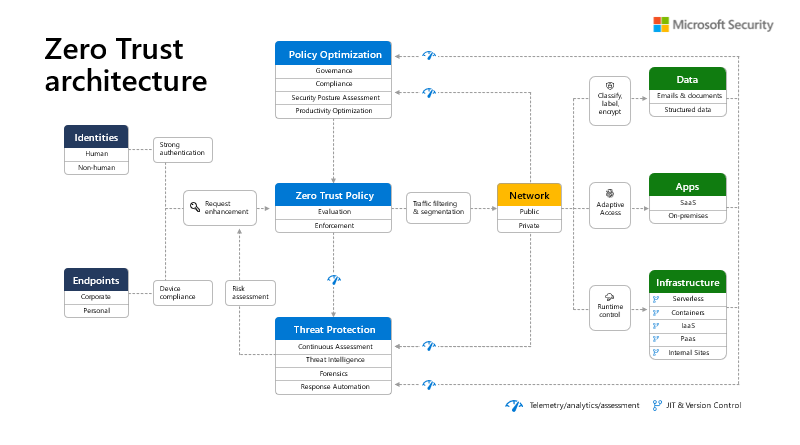
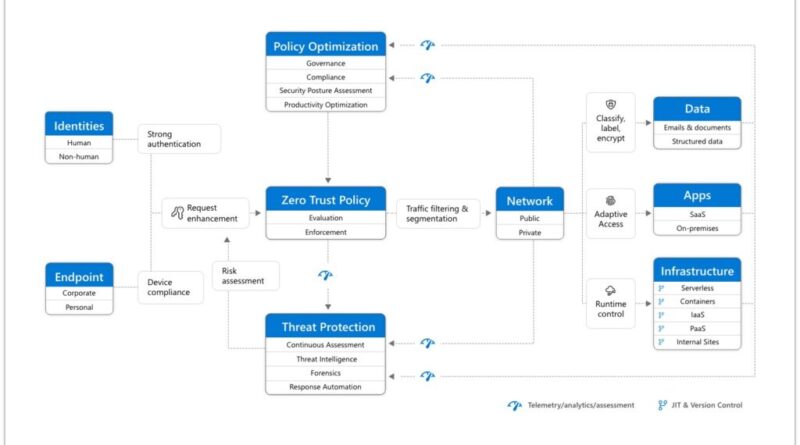
Breaches of sensitive data are extremely costly for organizations when you tally data loss, stock price impact, and mandated fines from violations of General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), or other regulations. They also can diminish the trust of those who become the victims of identity theft, credit card fraud, or…
The post Microsoft shares 4 challenges of protecting sensitive data and how to overcome them appeared first on Microsoft Security Blog. READ MORE HERE…