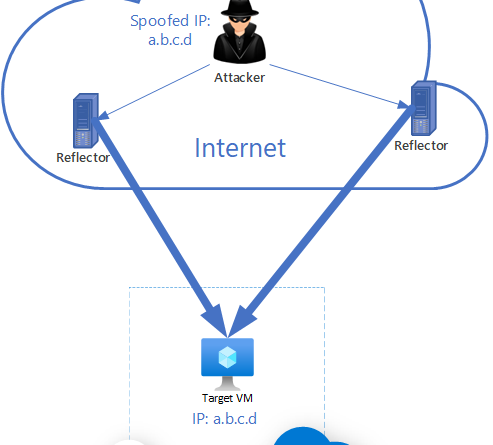
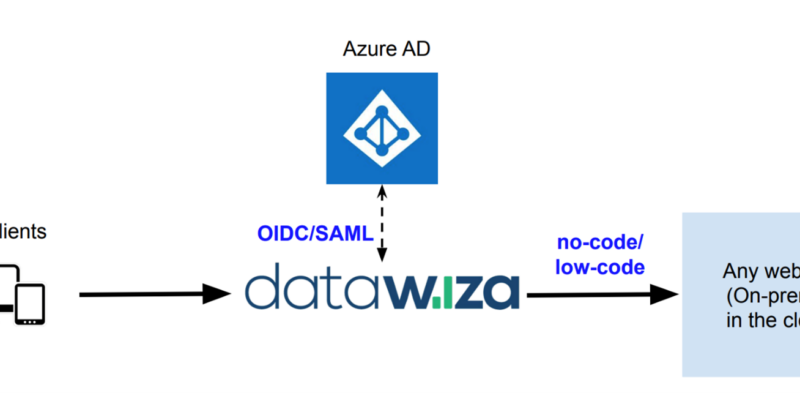
Anatomy of a DDoS amplification attack
Amplification attacks are one of the most common distributed denial of service (DDoS) attack vectors. These attacks are typically categorized as flooding or volumetric attacks, where the attacker succeeds in generating more traffic than the target can process, resulting in exhausting its resources due to the amount of traffic it receives.
The post Anatomy of a DDoS amplification attack appeared first on Microsoft Security Blog. READ MORE HERE…