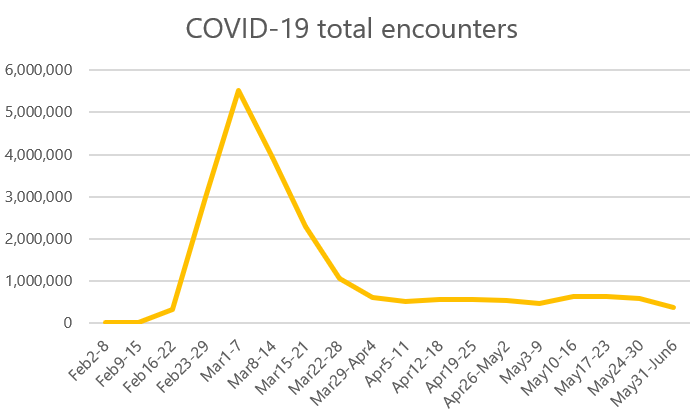
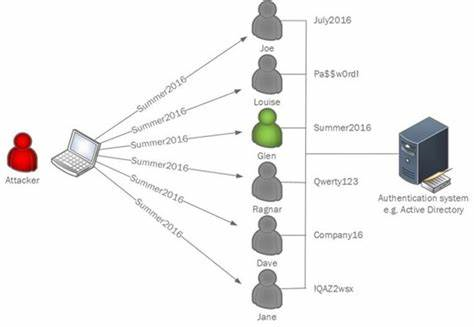
5 cybersecurity paradigm shifts that will lead to more inclusive digital experiences
Cybersecurity has proven to be the foundation for digital empathy in a remote workforce.
The post 5 cybersecurity paradigm shifts that will lead to more inclusive digital experiences appeared first on Microsoft Security. READ MORE HERE…