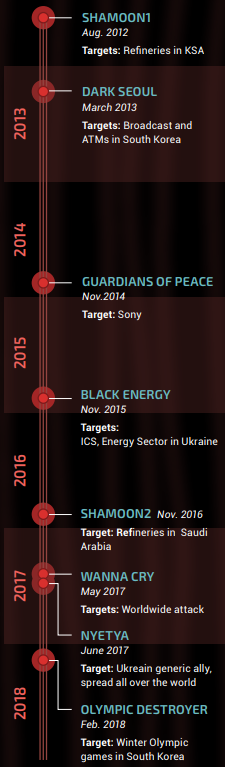
Secrets of the Wiper: Inside the World’s Most Destructive Malware
The actors behind this kind of code, whether they’re bent on sending a political message or simply wanting to cover their tracks after data exfiltration, have adopted various techniques to carry out those activities. READ MORE HERE…