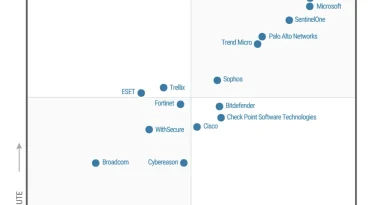
Microsoft is named a Leader in the 2025 Gartner® Magic Quadrant™ for Endpoint Protection Platforms

Since 2022, the number of human-operated ransomware-linked encounters by organizations surged by 2.75x. Yet, Microsoft Defender for Endpoint has outpaced this rise, reducing the number of successful attacks by 3x, proving its power to turn the tide against evolving cyberthreats.1
Defender for Endpoint’s ability to disrupt ransomware at scale stems from our commitment to empowering security analysts against the most sophisticated cyberthreats. We are honored to be recognized once again as a Leader in the 2025 Gartner® Magic Quadrant™ for Endpoint Protection Platforms—our sixth consecutive time. Microsoft was recognized for its completeness of vision and ability to execute, which we believe underscores the effectiveness of Defender for Endpoint in the face of an ever-shifting digital threat environment.
Microsoft Defender for Endpoint is an endpoint security solution that helps organizations secure their digital estate using AI-powered, industry-leading endpoint detection and response across Windows, Linux, macOS, Android, iOS, and Internet of Things (IoT) devices. It is core to Microsoft Defender’s unified security operations platform and built on global threat intelligence informed by more than 84 trillion daily signals and more than 10,000 security experts.1
We thank our customers and partners for their essential role in advancing Microsoft Security. The report will be available by July 17, 2025 for insights into our recognition as a Leader in the endpoint protection platform industry.
Over the past year, Microsoft has introduced key advancements to endpoint security that have empowered defenders to stay ahead of evolving cyberthreats, including:
- Proactively securing digital environments with exposure management capabilities spanning pre-to-post breach: Reducing exposure risks like vulnerabilities and misconfigurations is foundational to endpoint security. Defender for Endpoint’s unique visibility into a device estate helps security operations center (SOC) analysts see and harden against their organization’s level of exposure to weaknesses and exploits with an actionable risk score (endpoint security initiative). In the case of a cyberattack, analysts can further protect the organization and accelerate response with potential attack paths embedded into the incident. Analysts gain end-to-end visibility into attack paths bad actors may take across devices to reach high-value assets, enabling fast, informed decisions when it matters most.
- Disrupting ransomware attacks even earlier in the cyberattack chain with automatic attack disruption: Unique to Microsoft, automatic attack disruption is a built-in self-defense capability that contains in-progress cyberattacks to prevent further lateral movement and damage to an organization. The most pervasive cyberthreat to network-connected devices is ransomware, one of the many scenarios covered by attack disruption. Up to 90% of successful ransomware campaigns leverage unmanaged endpoints, which are typically personal devices that people bring to work.1 Automatic attack disruption now extends to unmanaged shadow IT devices and critical assets. Defender for Endpoint can detect and contain malicious IP addresses associated with unmanaged or undiscovered devices. It stops threat actors from exploiting vulnerable entry points, preventing lateral movement before it starts. Attack disruption now also granularly isolates cyberthreats on critical assets such as domain controllers, helping defenders preserve key network functions and ensure operational continuity during an attack.
- Enhancing Linux support: Microsoft supports even more Linux distributions, including ARM64 and has reduced resource requirements. These releases reflect the continual progress we’ve made for securing Linux servers on top of our strategic shift over a year ago to eBPF sensor technology that improves system control, minimizes resource demands, and boosts security performance. We’ve also continued delivering cross-platform innovation across Windows, macOS, iOS, Android, and IoT for comprehensive endpoint security.
- Unifying our agent across XDR workloads: The single agent makes it faster and easier to activate and manage core capabilities across endpoint, operational technology (OT), identity, and data loss prevention workloads so you can quickly unlock the value of AI-powered protection. Organizations simply deploy it once and then enable each solution as needed. Microsoft applies its long-established safe deployment practices in delivering the latest protections to help organizations outpace evolving cyberthreats without compromising operational stability. As a part of this process, admins have full control over these software updates.
- Accelerating SOC operations with Microsoft Security Copilot: It is the cybersecurity industry’s first generative AI solution, generally available as of April 2024. Built into the Microsoft Defender portal, it helps SOC analysts investigate, contain, and remediate cyberthreats in minutes. It delivers endpoint-specific capabilities such as recommending tailored guided responses related to devices, analyzing suspicious scripts, and translating natural language questions into ready-to-run Kusto Query Language (KQL) queries. Microsoft Security Copilot agents, introduced this year, automate routine tasks by fitting naturally into existing workflows across the security stack. These agents align to Microsoft’s Zero Trust principles, learn from feedback, and remain under SOC control.
- Supporting a global SOC: Security analysts navigate many complexities in their daily operations—language barriers should not be one of them. The Microsoft Defender portal provides experiences in more than 100 languages and dialects. Documentation covers more than 60 languages. This extensive language coverage ensures that analysts can easily navigate, understand, and act with confidence in their native tongue. Wherever the analyst is, Defender likely speaks their language.
- Extending your SOC team with Microsoft Defender Experts for XDR: Sophisticated threats span beyond endpoints. We’ve been continually enhancing the capabilities and improving the efficiencies of Microsoft Defender Experts for XDR, our managed XDR service. Defender Experts for XDR offers around-the-clocl, expert-led managed triage, investigation, and response across domains, along with proactive threat hunting—strengthening SOC capabilities around the clock.
Market leadership isn’t just about responding to current needs—it’s about driving the next wave of innovation. Microsoft is investing significantly in helping SOC teams quickly scale their endpoint defenses through foundational enhancements designed to radically simplify deployment and advanced AI-powered autonomous capabilities spanning pre-to-post breach, to name just a couple of highlights for what’s ahead.
Thank you to all our customers and partners. Your partnership drives our mission forward as we work side by side to build a safer, more secure world.
Learn more
If you’re not yet taking advantage of Microsoft’s leading endpoint security solution, visit Microsoft Defender for Endpoint and start a free trial today to evaluate our leading endpoint protection platform.
Are you a regular user of Microsoft Defender for Endpoint? Share your insights on Microsoft Defender for Endpoint and get rewarded with a $25 gift card on Gartner Peer Insights™.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and X (@MSFTSecurity) for the latest news and updates on cybersecurity.
1Microsoft Digital Defense Report 2024.
Gartner, Magic Quadrant for Endpoint Protection Platforms, Evgeny Mirolyubov, Deepak Mishra, Franz Hinner. July 14, 2025.
Gartner is a registered trademark and service mark and Magic Quadrant is a registered trademark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
READ MORE HERE