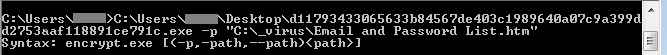
Collecting In the Dark: Tropic Trooper Targets Transportation and Government
Our long-term monitoring of the cyberespionage group Earth Centaur (aka Tropic Trooper) shows that the threat actors are equipped with new tools and techniques. The group seems to be targeting transportation companies and government agencies related to transportation. Read More HERE…