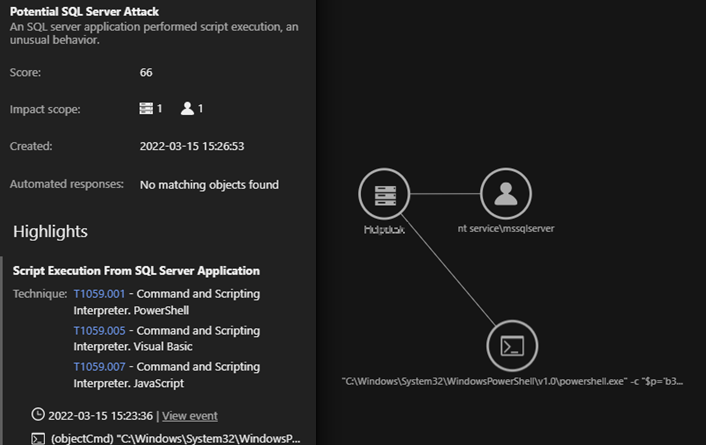
New Linux-Based Ransomware Cheerscrypt Targeting ESXi Devices Linked to Leaked Babuk Source Code
New findings showed that Cheerscrypt, a new Linux-based ransomware variant that compromises ESXi servers, was derived from the leaked Babuk source code. We discuss our analysis in this report. Read More HERE…