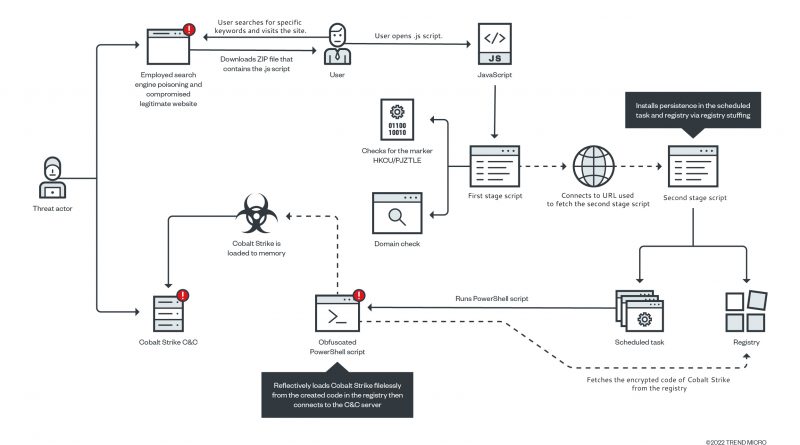
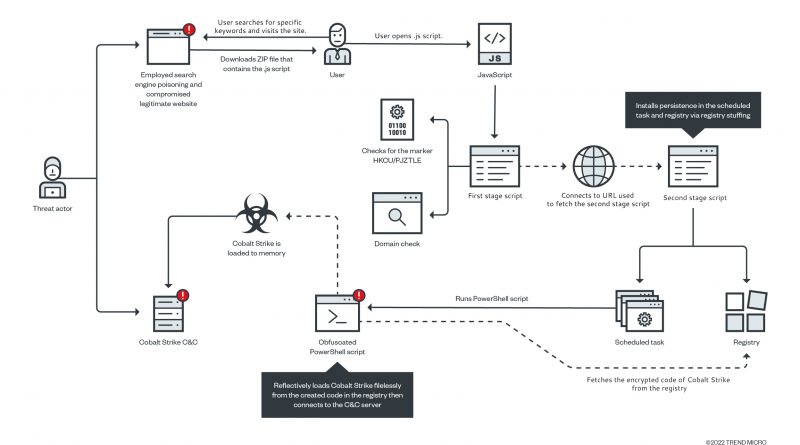
SolidBit Ransomware Enters the RaaS Scene and Takes Aim at Gamers and Social Media Users With New Variant
This blog entry offers a technical analysis of a new SolidBit variant that is posing as different applications to lure gamers and social media users. The SolidBit ransomware group appears to be planning to expand its operations through these fraudulent apps and its recruitment of ransomware-as-a-service affiliates. Read More HERE…