TrendMicro
Unpacking the Structure of Modern Cybercrime Organizations
We examine three differently sized criminal groups to know how they compare to similarly sized legitimate businesses in terms of how they are organized. We also discuss how threat researchers can use their knowledge of the size and structure of a target criminal organization to aid their investigation. Read More HERE…
S4x23 Review Part 4: Cybersecurity for Industrial IoT
In this fourth article, I introduce the discussion related to Industrial IoT, that is involved challenges to adopt cybersecurity strategy into modernizing environment. Read More HERE…
Developing Story: Information on Attacks Involving 3CX Desktop App
In late March 2023, security researchers revealed that threat actors were actively abusing a popular business communication software from 3CX. Read More HERE…
3 Shifts in the Cyber Threat Landscape
The threat landscape is always changing and these three major shifts are already underway. Learn to recognize them to protect your organization from cyber threats. Read More HERE…
Mac Malware MacStealer Spreads as Fake P2E Apps
We detected Mac malware MacStealer spreading via websites, social media, and messaging platforms Twitter, Discord, and Telegram. Cybercriminals lure victims to download it by plagiarizing legitimate play-to-earn (P2E) apps’ images and offering jobs as beta testers. Read More HERE…
Preventing and Detecting Attacks Involving 3CX Desktop App
In late March 2023, security researchers revealed that threat actors were actively abusing a popular business communication software from 3CX. Read More HERE…
Fighting mercenaries with the Cybersecurity Tech Accord
Trend Micro co-Authors Cyber Mercenary Principles to help guide the technology industry and others in dealing with the growing market of cyber mercenaries. Read More HERE…
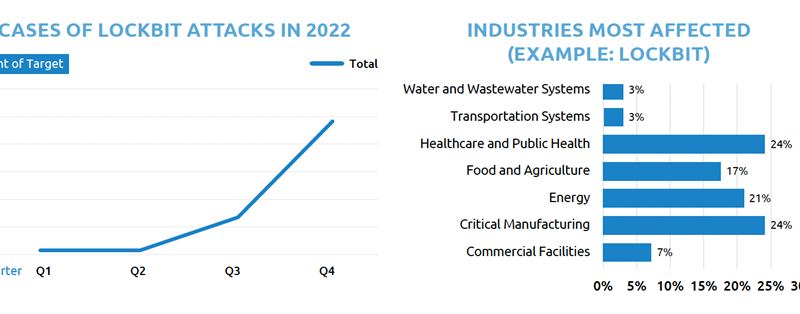
ICS/OT Cybersecurity 2022 TXOne Annual Report Insights
This article gives an in-depth overview of TXOne’s insight report on ICS/OT cyber incidents. Read More HERE…
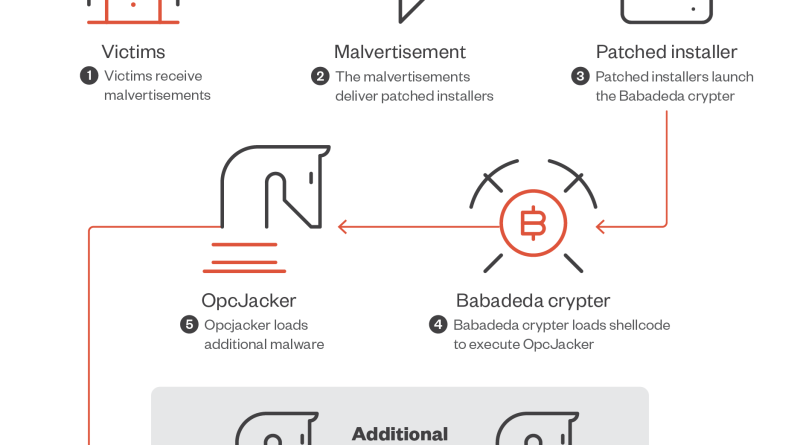
New OpcJacker Malware Distributed via Fake VPN Malvertising
We discovered a new malware, which we named “OpcJacker” (due to its opcode configuration design and its cryptocurrency hijacking ability), that has been distributed in the wild since the second half of 2022. Read More HERE…