TrendMicro
How Zero Trust Can Help Your Organization: Strengthening Security and Supply Chain Assurance
In this article, we will explore how Zero Trust can benefit your organization, focusing on its ability to enhance security, secure supply chains, and align with international regulatory frameworks. Read More HERE…
The Well-Architected Framework Guide
Discover the six Amazon Web Services (AWS) pillars by examining best practices and design principles to leverage the cloud in a more efficient, secure, and cost-effective manner. Read More HERE…
An Overview of the Different Versions of the Trigona Ransomware
The Trigona ransomware is a relatively new ransomware family that began activities around late October 2022 — although samples of it existed as early as June 2022. Since then, Trigona’s operators have remained highly active, and in fact have been continuously updating their ransomware binaries. Read More HERE…
How to Deploy Generative AI Safely and Responsibly
New uses for generative AI are being introduced every day—but so are new risks. Read More HERE…
How to Implement a Secure API Gateway
As you rely more on APIs to connect microservices in modern applications, these APIs become a lucrative target for bad actors. Learn how an API gateway provides an extra layer of security, helping protect your systems and data from unauthorized access. Read More HERE…
How to Write a Cybersecurity Policy for Generative AI
Just months after hitting the scene, generative AI already seems like it will become a permanent addition to the enterprise IT toolbox. For CISOs, the pressure is on to roll out AI security policies and technologies that can mitigate very real and present risks. Read More HERE…
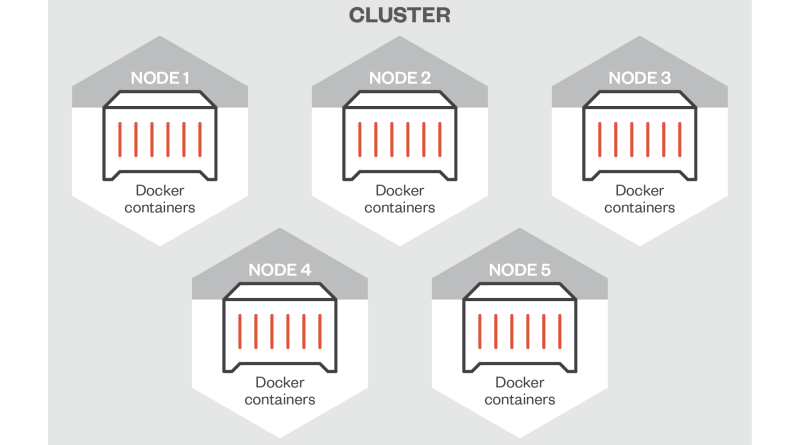
Gaps in Azure Service Fabric’s Security Call for User Vigilance
In this blog post, we discuss different configuration scenarios that may lead to security issues with Azure Service Fabric, a distributed platform for deploying, managing, and scaling microservices and container applications. Read More HERE…
MOVEit Vulnerability Breaches Targeted Fed Agencies
Jon Clay and Ed Cabrera talk about the MOVEit breaches and more in the video series #TrendTalksBizSec Read More HERE…