Sophisticated new Android malware marks the latest evolution of mobile ransomware
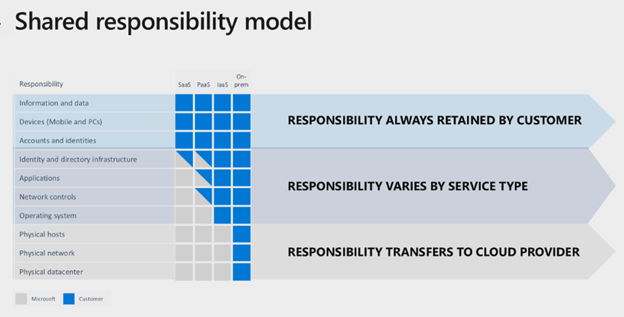
We found a piece of a particularly sophisticated Android ransomware with novel techniques and behavior, exemplifying the rapid evolution of mobile threats that we have also observed on other platforms.
The post Sophisticated new Android malware marks the latest evolution of mobile ransomware appeared first on Microsoft Security. READ MORE HERE…