The five-day job: A BlackByte ransomware intrusion case study
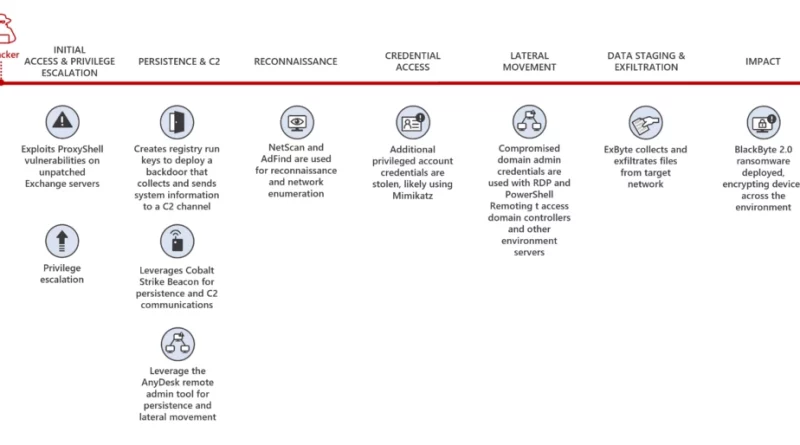
In a recent investigation by Microsoft Incident Response of a BlackByte 2.0 ransomware attack, we found that the threat actor progressed through the full attack chain, from initial access to impact, in less than five days, causing significant business disruption for the victim organization.
The post The five-day job: A BlackByte ransomware intrusion case study appeared first on Microsoft Security Blog. READ MORE HERE…