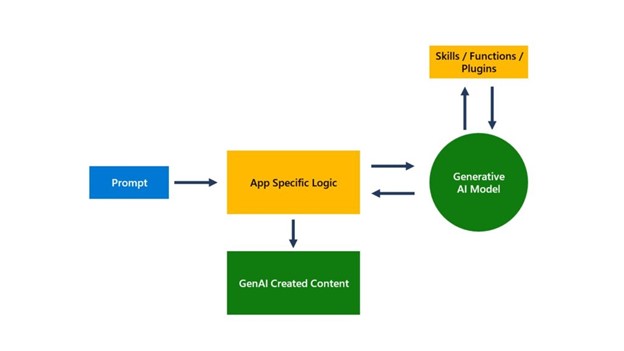
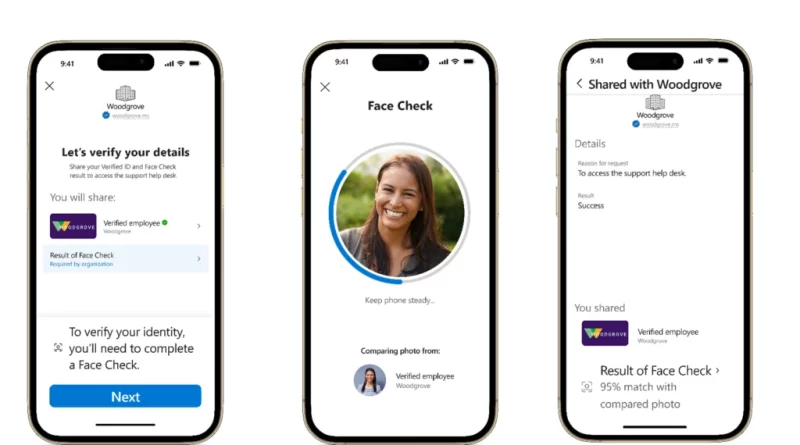
Microsoft Secure: Learn expert AI strategy at our online event
Microsoft Secure is a two-hour digital showcase of the latest technology innovations, including Microsoft Copilot for Security. Register today to reserve your spot.
The post Microsoft Secure: Learn expert AI strategy at our online event appeared first on Microsoft Security Blog. READ MORE HERE…