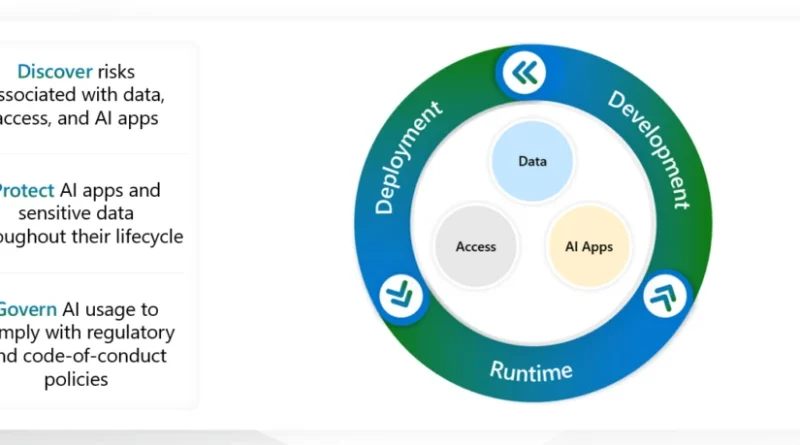
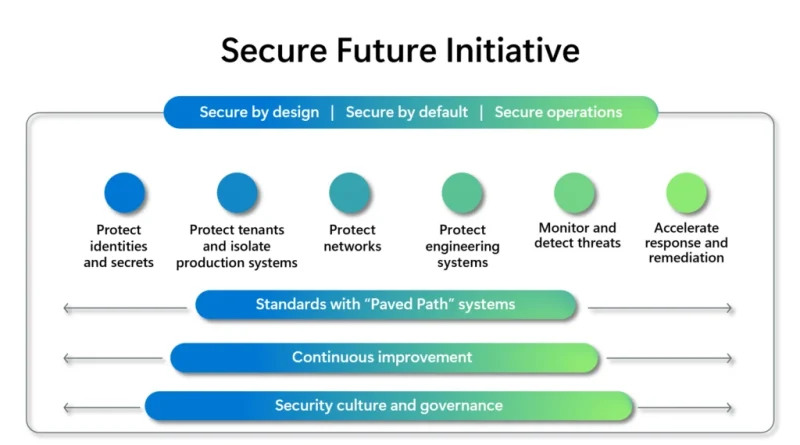
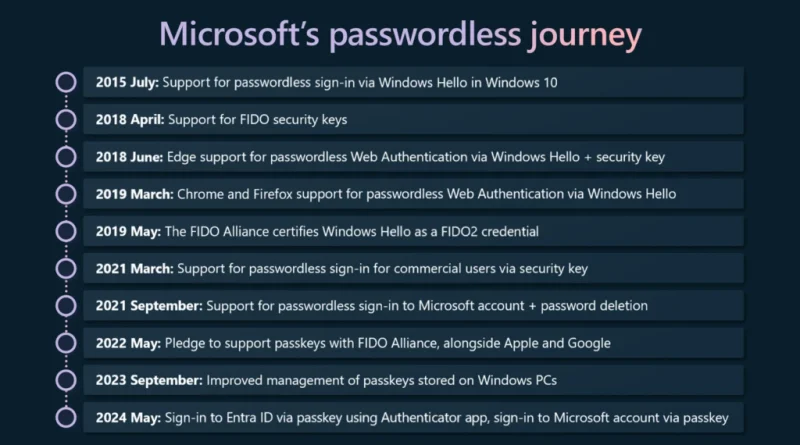
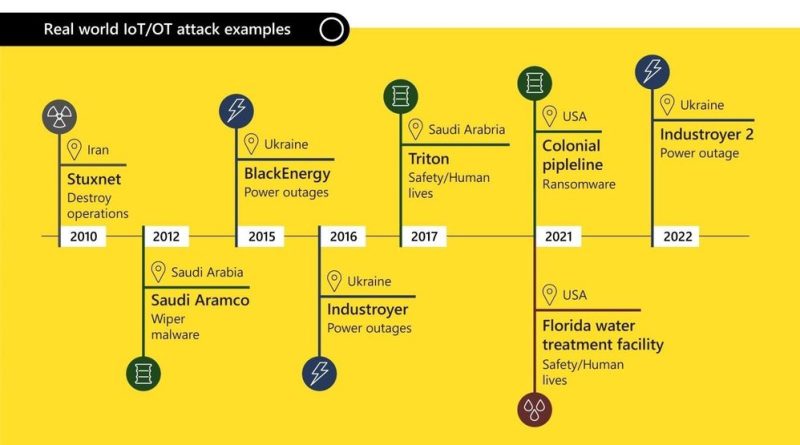
Microsoft announces the 2024 Microsoft Security Excellence Awards winners
At this year’s Microsoft Security Excellence Awards, we took a journey through the evolution of cybersecurity from the 1950s to today. While this event theme celebrated the significant technological advancements that have shaped each decade, the main focus was on the Microsoft Intelligent Security Association (MISA) member finalists and winners whose innovations in cybersecurity have earned them well-deserved recognition.
The post Microsoft announces the 2024 Microsoft Security Excellence Awards winners appeared first on Microsoft Security Blog. READ MORE HERE…