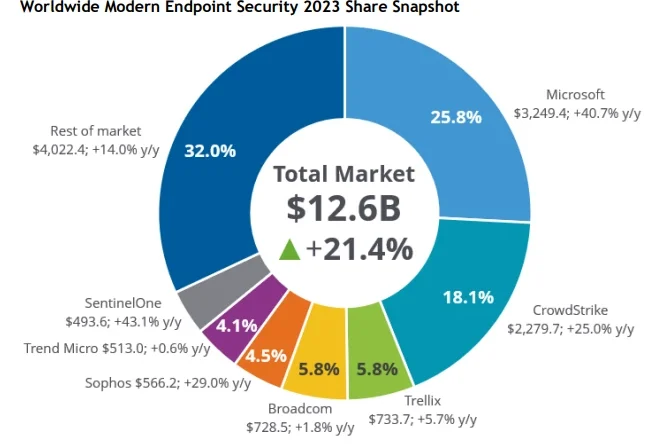
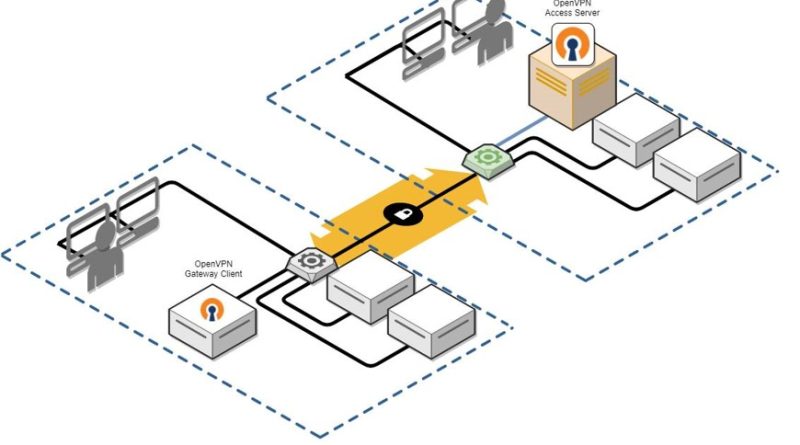
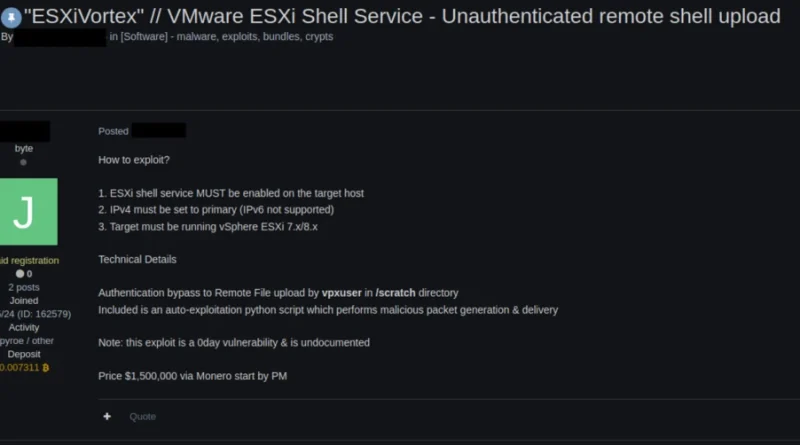
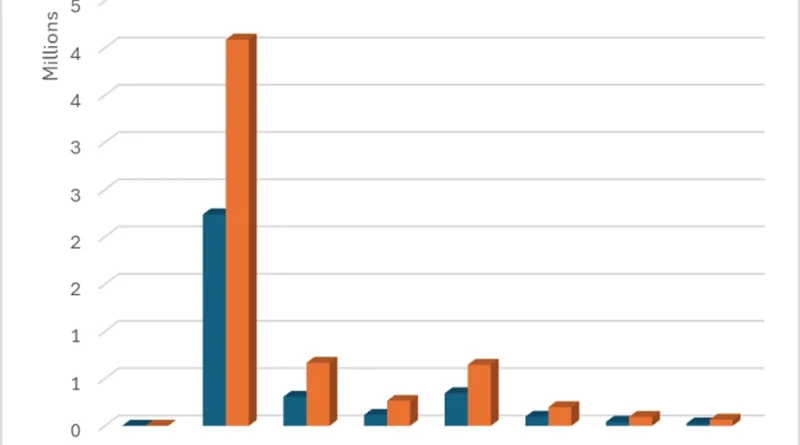
Microsoft AI Tour: Hear the latest product innovations to elevate your security strategy
The Microsoft AI Tour is coming to a city near you. Join a free, one-day tour event to learn how we are making AI deployment more secure.
The post Microsoft AI Tour: Hear the latest product innovations to elevate your security strategy appeared first on Microsoft Security Blog. READ MORE HERE…