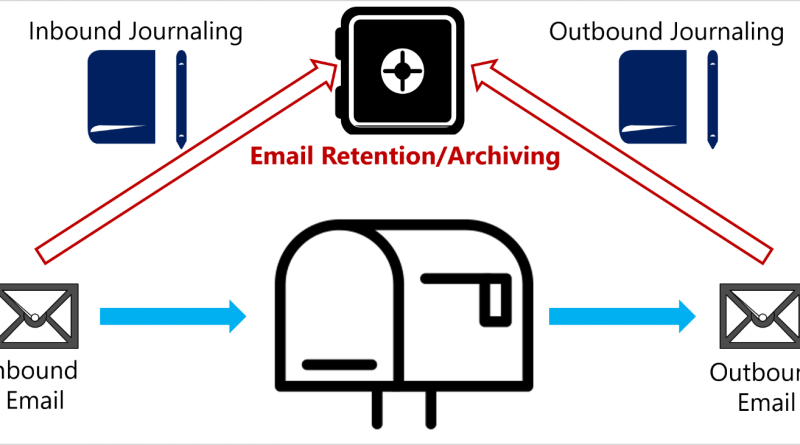
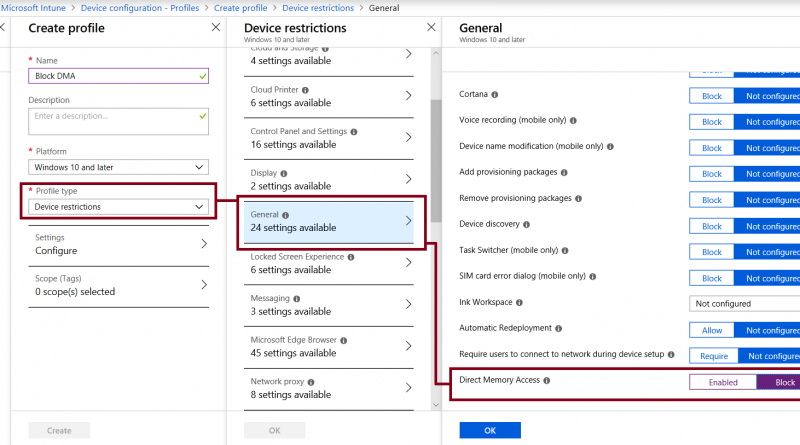
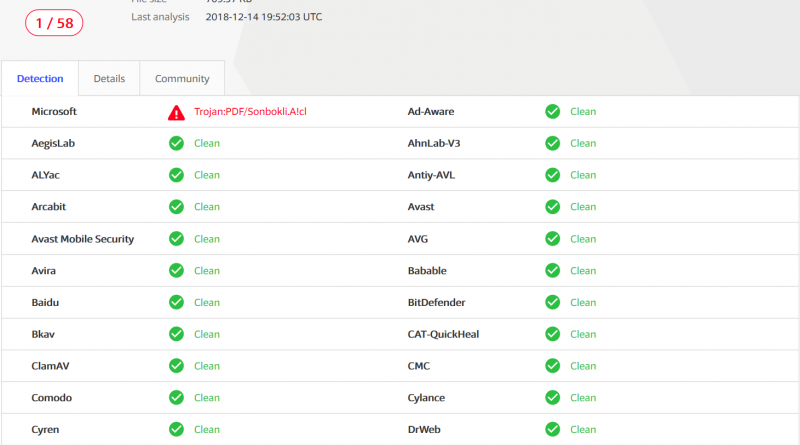
Microsoft gains strong customer and analyst momentum in the Cloud Access Security Brokers (CASB) market
Microsoft jumped to the Challenger position in the Gartners 2018 Magic Quadrant for CASB and solidified its Leadership position in KuppingerColes 2018 Leadership Compass in the same product category.
The post Microsoft gains strong customer and analyst momentum in the Cloud Access Security Brokers (CASB) market appeared first on Microsoft Secure. READ MORE HERE…