Analyzing a Multi-Stage AsyncRAT Campaign via Managed Detection and Response

- AsyncRAT-connected threat actors are exploiting Cloudflare’s free-tier services and TryCloudflare tunneling domains to host their WebDAV servers, masking malicious activities under trusted infrastructure and making detections challenging for traditional security solutions while ensuring reliable payload delivery.
- The attack uses legitimate Python downloads from official sources, establishing a complete Python environment on victim systems to execute sophisticated code injection techniques targeting explorer.exe processes.
- The campaign begins with phishing emails distributed via Dropbox links, using double-extension files (.pdf.url) to deceive victims, and displaying legitimate PDF documents during execution to reduce suspicion.
- The malware ensures persistence through multiple vectors including startup folder scripts (ahke.bat, olsm.bat), WebDAV mounting, and legitimate “living-off-the-land” techniques using Windows Script Host, PowerShell, and built-in system utilities to evade detection.
- Trend Vision One™ detects and blocks the indicators of compromise (IOCs) outlined in this blog, and provides customers with tailored threat hunting queries, threat insights, and intelligence reports.
AsyncRAT has emerged as a notable Remote Access Trojan (RAT) used by threat actors for its robust capabilities and ease of deployment. It gained favor for its extensive feature set, which includes keylogging, screen capturing, and remote command execution capabilities. Its modular architecture, typically implemented in Python, provides flexibility and ease of customization, making it a preferred tool of choice for cybercriminals.
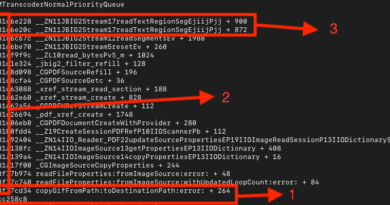
During our investigation of AsyncRAT infections, we observed Python scripts playing a central role in the infection chain, automating various stages of the attack. The initial payload, a Windows Script Host (WSH) file, was designed to download and execute additional malicious scripts hosted on a WebDAV server. These scripts facilitated the download of batch files and further payloads, ensuring a seamless and persistent infection routine.
The attackers cleverly exploited Cloudflare’s free-tier services to host their WebDAV server, abusing the platform’s reliability and widespread trust to evade detection. By using Cloudflare’s infrastructure, the threat actors masked the malicious activity under legitimate domains, making it challenging for traditional security solutions to identify and block the threat.
Similar behavior was documented before by other researchers. However, since then there have been changes in the behavior of the scripts, as well as differing main payloads.
This entry dissects the attack chain from initial compromise through AsyncRAT deployment, examining the attacker’s techniques for system infiltration and persistent access.
Figure 1 illustrates the observed behavior of the threat across the cases we investigated. During the initial stages of the attack, users received a phishing email containing a Dropbox link leading to an Internet Shortcut file(.url). When opened, the file redirects users to download multi-stage scripts hosted on TryCloudflare domains. These scripts then install a Python environment, establish persistence via startup folder scripts, and inject code into explorer.exe. The final payload (new.bin) was identified to be AsyncRAT.
Read More HERE