Watering Hole Attack Targets EmEditor Users with Information-Stealing Malware

Based on its geofencing behavior, we assess that the threat actors are likely of Russian origin, or those from the Commonwealth of Independent States (CIS). This aligns with a common pattern observed among groups from this region, where “friendly” countries are excluded to reduce legal and operational risk. It excludes:
- Armenia
- Belarus
- Georgia
- Kazakhstan
- Kyrgyzstan
The malware sends all collected information to its C&C server at:
- hxxps://cachingdrive[.]com/gate/init/2daef8cd.
Another notable detail we saw is the consistent presence of the unique string “2daef8cd” on its communication, suggesting that it may likely resemble some sort of Campaign ID.
As of now, there are already a few recorded instances of the URL being accessed by EmEditor users, suggesting that some have already been likely compromised prior to the company’s announcement.
Security best practices again software supply chain attacks
This incident challenges longstanding assumptions that trusted software can be treated as lower priority during triage, and that installations — even from official vendors — is inherently less risky than exploit-driven intrusion. The following best practices can help organizations strengthen their ability to detect and contain this kind of threat:
- Validate installer integrity. Confirm digital signatures and perform file integrity checks before execution, even when installers are downloaded from official vendor sites. Where possible, compare against a trusted reference to detect tampering or unauthorized modification.
- Govern usage of PowerShell. Apply controls around PowerShell execution and enable robust logging. Monitor for obfuscated scripts and network-enabled commands, which are commonly abused for payload retrieval and staging.
- Preserve endpoint telemetry and visibility. Actively monitor for attempts to disable or interfere with logging mechanisms. Protecting telemetry helps maintain detection coverage when attackers attempt to operate with reduced visibility.
- Enforce the principle of least privilege to credentials and networks. Limit which processes and accounts can access credential storage and restrict where privileged credentials can be used. Monitor authentication activity for anomalies and attempted lateral movement.
For developers and software publishers, this kind of attack shows that protecting how software is built and delivered is just as important as securing the application itself:
- Secure download and hosting infrastructure. Apply strict access controls and monitoring to download servers and back-end storages. Monitor for unexpected file changes, redirects, or modifications that could indicate tampering with distributed installers.
- Publish verifiable integrity information. Provide file integrity information and make verification steps explicit so that users can confirm installer authenticity prior to execution.
- Prepare an incident response plan. Define procedures for responding to suspected supply chain compromise, including takedown of affected installers, certificate revocation, user notification, and coordination with security vendors.
Proactive security with TrendAI Vision One™
TrendAI Vision One™ is the industry-leading AI cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection.
TrendAI Vision One™ Threat Intelligence Hub provides the latest insights on emerging threats and threat actors, exclusive strategic reports from TrendAI™ Research, and TrendAI Vision One™ Threat Intelligence Feed in the TrendAI Vision One™ platform.
Emerging Threats:
Watering Hole Attack Targets EmEditor Users With Information-Stealing Malware
Watering Hole Attack Targets EmEditor Users With Information-Stealing Malware
Hunting Queries
TrendAI Vision One™ customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
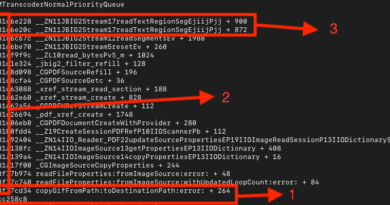
EMEDITOR Command Lines:
processCmd:(powershell AND (emeditorjp.com OR emeditorgb.com/run/mg8heP0r OR emeditorde.com/gate/start/2daef8cd OR cachingdrive.com/gate/init/2daef8cd))
More hunting queries are available for TrendAI Vision One™ with Threat Intelligence Hub entitlement enabled.
Indicators of Compromise (IOCs)
The indicators of compromise for this entry can be found here.
Read More HERE