The Real Frontiers for 2021 in XDR
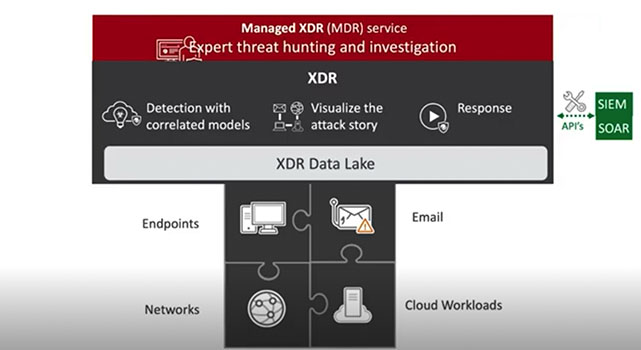

In a perfect world, you require fast detection and response across the entire IT environment. But if your SOC is getting data in silos, which is the case for a lot of companies, they will probably have to use EDR to get detailed visibility for suspicious activity on endpoints, then a separate siloed view of network security alerts and traffic analysis, and so on. Each product will end up producing its own perspective of the attack—no correlated information or a consolidated view of the entire chain of events. And often, you’ll get differing levels of detail to make it even harder to connect the dots.
Cue XDR
This is where extended detection and response, or XDR, technology comes in, linking together data from email, servers, endpoints, cloud workloads, and networks to tell the whole story of the attack—as promised. The XDR approach delivers faster detection and response across the whole environment, as it breaks down the silos and tells the full story instead of making the SOC team dig through noisy alerts and then try and figure out how to respond in the many different consoles. XDR gets telemetry from the entire IT environment, using automation and big data to build the story and save time for the SOC.
Unlike an API approach, where you are limited to querying the siloed data sets, information can be pooled in a cloud data lake to enable deeper analysis and generate insights that you may not have even known to look at. With the correlated detection from XDR technology, you can automatically filter out the “low-confidence” events, behaviors, and actions within or across security layers, using machine learning, data stacking, and other big data analysis techniques to create a bigger picture and take action quickly. Because when you can confidently see and protect your entire technology landscape, you can empower your business in new, strategic ways.
Mapping to MITRE ATT&CK
Many organizations are starting to use MITRE ATT&CK to improve their security operations by making sure they are adequately equipped for common adversarial behavior. MITRE ATT&CK collects and categorizes common attack tactics, techniques, and procedures (TTPs), then organizes this information into a framework. When it comes to XDR solutions, you gain more context with mapping to the MITRE ATT&CK framework for faster detection and higher fidelity alerts. This framework can be used to help explain how adversaries behave, what they are trying to do, and how they are trying to do it. In fact, MITRE ATT&CK recently tested against APT29 with some very interesting results.
Leverage your people
With the predominant skills gap in the industry, you want the personnel you have to be able to work on meaningful tasks. However, that is a bit hard with the barrage of alerts from single-vector solutions consuming their day. By automatically correlating threat data from multiple sources, XDR speeds up and removes manual steps involved in investigations and enables security analysts to quickly find the full story of an attack. Removing the low-confidence events and repetitive tasks frees them to be able to work on the valuable projects that are required to secure the organization and leave you with peace of mind.
Hear more on the real frontier for 2021 in XDR.
- Casey, T. (2018, May 28). Survey: 27 Percent of IT professionals receive more than 1 million security alerts daily: Imperva. Retrieved from https://www.imperva.com/blog/27-percent-of-it-professionals-receive-more-than-1-million-security-alerts-daily/
- Oltsik, J. and Clark, J, (2020, August). Security Infrastructure and Market Changes in Progress, Enterprise Strategy Group
Read More HERE




