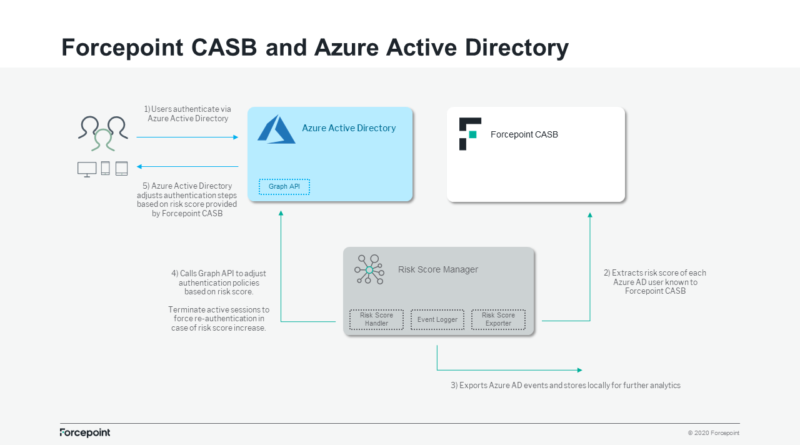
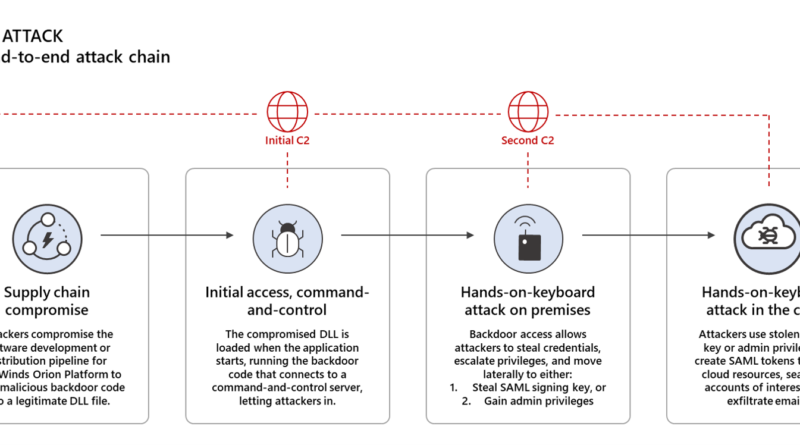
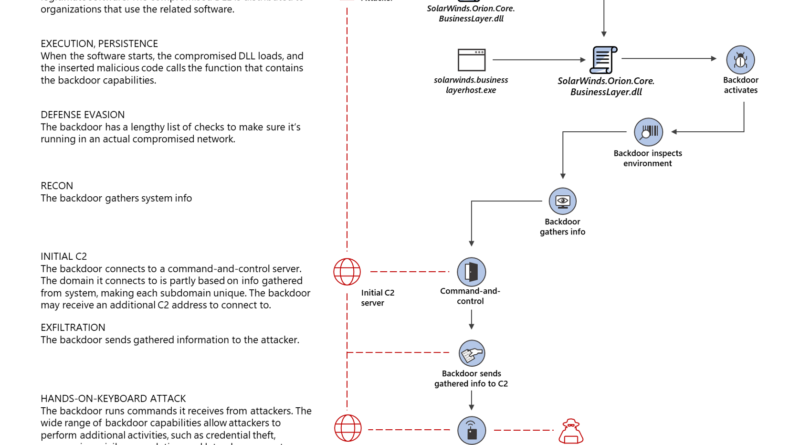
Wi-Fi Protected Access 3 (WPA3) has brought significant security improvements to Wi-Fi networks, particularly WPA-3Enterprise, which includes tweaks to make authenticating to the network more secure. One of these is has to do with 802.1x authentication that is used to determine whether Wi-Fi clients will be granted access to the enterprise network.
Wi-Fi resources
Test and review of 4 Wi-Fi 6 routers: Who’s the fastest?
How to determine if Wi-Fi 6 is right for you
Five questions to answer before deploying Wi-Fi 6
Wi-Fi 6E: When it’s coming and what it’s good for
The enterprise mode of WPA has always allowed you to give each user a unique username/password to login to the Wi-Fi or to utilize unique digital certificates for each user to install on devices for even more security. Now with WPA3-Enterprise, the security is increased as clients are now required to make sure it’s communicating with the real authentication server before sending login credentials. That verification was optional with the earlier two versions of WPA.To read this article in full, please click here READ MORE HERE…
Read More